Cloud Storage Profiles
Signiant Jet currently supports Amazon AWS storage as a source or destination endpoint, allowing file transfers between on-premises SDCX Servers and cloud-based SDCX Servers. In order to use Amazon AWS, you must either provide a Role ARN or an Access Key ID and a Secret Access Key to allow access to your storage buckets.
Authentication Methods
Jet supports two options to allow access to Amazon AWS buckets:
-
A Role ARN provides access to storage based on an access policy which can be scoped to a specific bucket and permission level.
-
An Access Key and associated Secret Access Key provide a way to grant access to any storage bucket in your AWS account but cannot be scoped to a specific bucket and permission level.
Role ARN Authentication
An Amazon Resource Name (ARN) is a way to identify a particular permission set for AWS resources. ARNs help an administrator track and allow the use of policies across AWS products.
Creating a Policy
To create a Role ARN, you must create and configure a limited access policy using Amazon Identity and Access Management, IAM.
-
In the Amazon AWS console, go to IAM and click Policies to open the Policies page.
-
Click Create policy.
- In the Policy Editor, click to open the JSON tab.
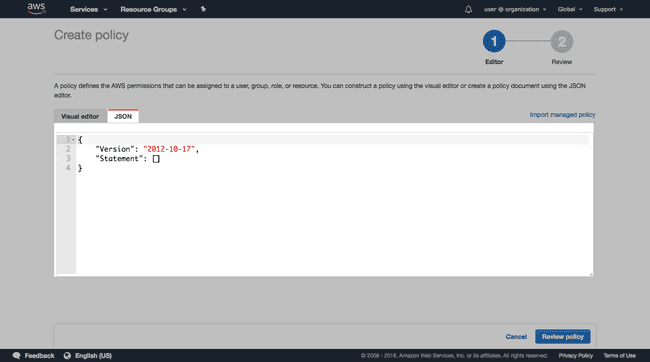
- Copy and paste the following Policy into the JSON code editor:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "SigniantJetConsoleActions",
"Action": [
"s3:ListAllMyBuckets",
"s3:GetBucketLocation"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Sid": "SigniantJetXferEngineActions",
"Effect": "Allow",
"Action": [
"s3:AbortMultipartUpload",
"s3:DeleteObject*",
"s3:GetObject*",
"s3:ListBucket*",
"s3:ListMultipartUploadParts",
"s3:PutObject*",
"s3:GetBucketLocation"
],
"Resource": [
"arn:aws:s3:::*",
"arn:aws:s3:::*/*"
]
}
]
}The SigniantJetXferEngineActions in the code sample allows access to all S3 buckets. To specify a single bucket, edit the Resource array and specify a bucket name:
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name>/*"
]-
Click Review policy.
-
Enter a Name and Description for the policy.
-
Click Create policy.
The default policy grants Signiant Jet the permission to list all S3 buckets when adding a storage profile. The s3:ListAllMyBuckets permission can be omitted.
Create an ARN
-
In Amazon AWS, go to IAM and click Roles to open the Roles menu.
-
Click Create role.
- Select Another AWS account as the trusted entity.
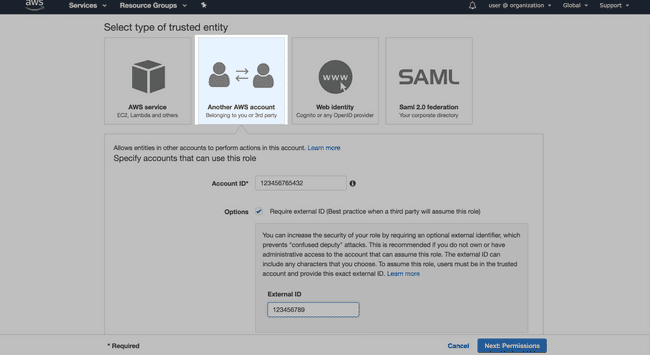
- Enter the Signiant Account ID provided on the Create AWS S3 Storage Profile page.
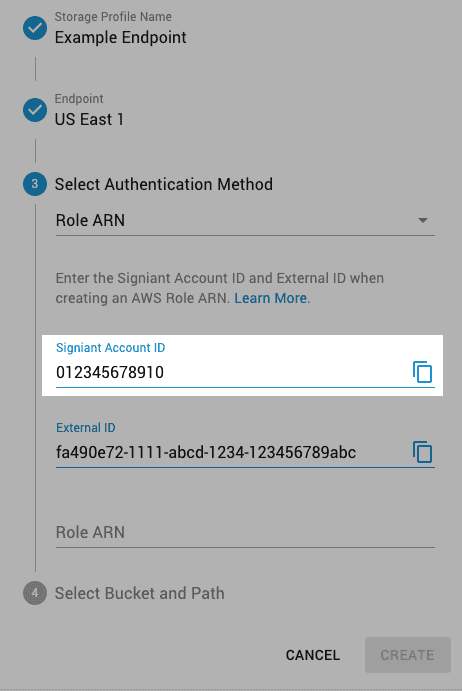
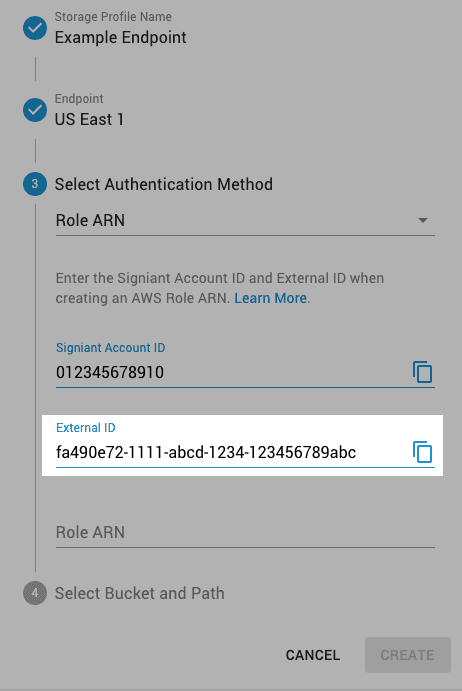
- Enable Require external ID, and enter the External ID provided with the Signiant Account ID.
-
Click Next: Permissions.
-
On the Attach permissions policies page, use the search to filter for the policy and select it using the check box.
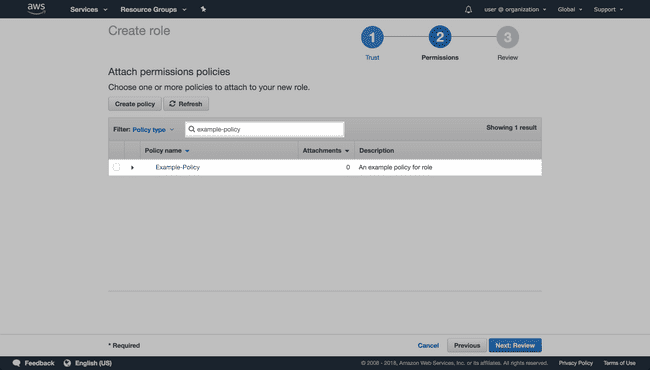
-
Click Next: Tags, followed by Next: Review.
-
Set the Name and Description for the Role ARN.
-
Click Create Role.
After creating the role, open its summary via the Roles page, copy the Role ARN to your clipboard, and paste it in the Role ARN field in the Jet management Console.
Access Key Authentication
Selecting the Access Key option allows the use of an Access Key ID and associated Secret Access Key to authorize Jet to access your account, allowing you to select a bucket to use as a storage profile.
Note: The storage profile bucket must be in the specified endpoint region.
For more information about obtaining Access Key IDs and Secret Access Keys, see the Amazon AWS documentation.
Creating a Storage Profile
Once you have determined your authentication method, create a storage profile.
To create a storage profile on an SDCX Server:
-
In the Jet management console, click Storage.
-
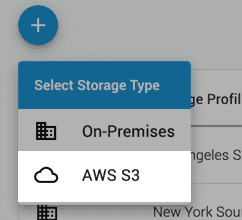
Click the Add button and select AWS S3.
-
On the Create AWS S3 Storage Profile page, enter a storage profile name.
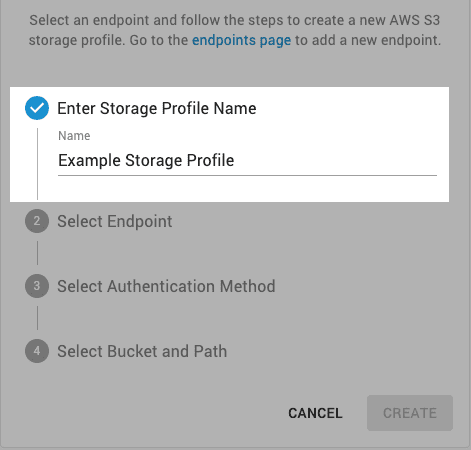
-
Select an Endpoint.
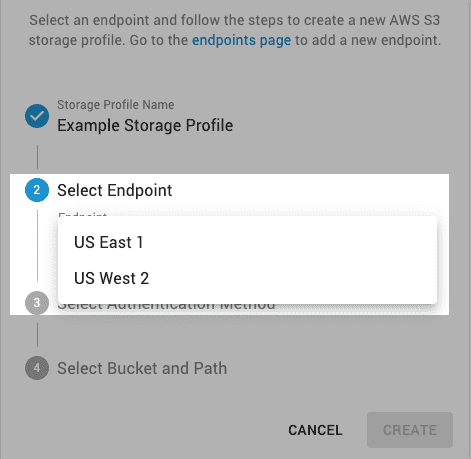
-
Select the Authentication Method: Access Key or Role ARN.
-
Enter the required credentials to access your AWS account.
-
Select a Bucket and set a Path (optional).
Note: If the
s3:ListAllMyBucketsis not included in your policy, you must enter the bucket name. -
Click Create.
Once the storage profile is created, the associated bucket can be used as a destination for any job.